
Your Organization’S Data Cannot Be Pasted Here.
Your organization’s data cannot be pasted here due to security restrictions. This ensures data confidentiality and protection.
In today’s digital age, data security is of utmost importance for organizations to safeguard sensitive information from potential threats. With the advancement of technology, the risk of data breaches has increased, making it crucial for companies to implement strict security measures.
When faced with the message “Your organization’s data cannot be pasted here,” it is a clear indication that the system is preventing unauthorized copying and pasting of data. This security protocol helps prevent data leakage and ensures that confidential information remains secure within the organization’s network. By adhering to these security restrictions, organizations can mitigate the risk of data breaches and maintain the integrity of their data assets.
Understanding Data Security
Data security is a critical aspect of every organization’s operations. Understanding and addressing potential data threats are essential for maintaining the integrity and confidentiality of sensitive information. In this section, we will delve deeper into the importance of data security and explore different types of data threats that can jeopardize your organization’s valuable data assets.
The Importance Of Data Security
Data security is of utmost importance as it safeguards sensitive information from unauthorized access, theft, and misuse. Ensuring robust data security measures not only protects the organization’s data but also instills trust among customers, partners, and stakeholders. In the event of a data breach, the repercussions can be severe, including financial losses, damaged reputation, and legal implications. Therefore, maintaining effective data security is indispensable for any organization.
Types Of Data Threats
- Malware: Malicious software designed to infiltrate and damage computer systems.
- Phishing: Deceptive techniques to acquire sensitive information such as login credentials and financial data.
- Data Theft: Unauthorized extraction or copying of confidential information by internal or external actors.
- Insider Threats: Risks posed by employees, contractors, or partners who misuse their access to sensitive data.
- Ransomware: Cyberattacks that encrypt data and demand ransom for its release.
Protecting Your Organization’s Data
Implementing Strong Password Policies
- Create complex passwords with a mix of letters, numbers, and symbols.
- Change passwords regularly to prevent unauthorized access to sensitive information.
Enforcing Two-factor Authentication
- Add an extra layer of security by requiring users to verify their identity through a second method.
- This minimizes the risk of breaches even if passwords are compromised.
Encrypting Sensitive Data
- Convert data into a code that can only be accessed with a decryption key.
- Protects sensitive information from being read by unauthorized individuals.
Monitoring And Auditing Data Access
- Regularly review who has access to data and what actions they are performing.
- Identify any unusual behavior that could indicate a security threat.
Educating Employees On Data Security
Educating employees on data security is crucial to protect your organization’s valuable information.
Raising Awareness On Data Security Practices
- Regularly conduct workshops to educate employees on the importance of data security.
- Create internal communication campaigns with tips for safe data handling.
- Post reminders in common areas about the significance of data protection.
Training Employees On Safe Data Handling
- Provide comprehensive training on handling confidential data securely.
- Offer guidance on encryption techniques to safeguard sensitive information.
- Ensure all employees are well-versed in company data security policies.
Simulating Phishing Attacks To Test Vigilance
- Conduct regular phishing attack simulations to gauge employees’ awareness.
- Provide feedback on employee responses and offer further training as needed.
- Encourage reporting of suspicious emails to enhance vigilance levels.
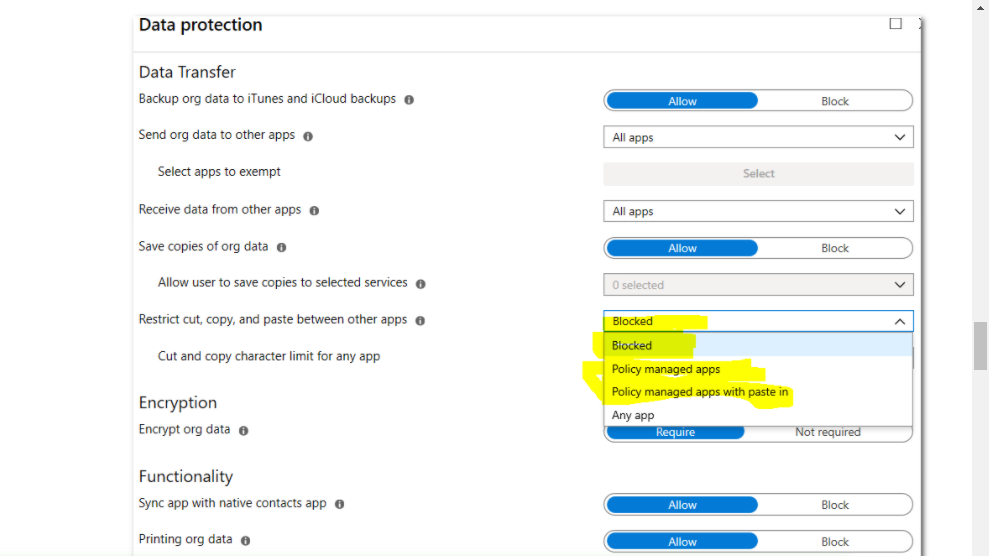
Credit: www.electronicshub.org
The Role Of It In Data Protection
Regular System Updates And Patching
Regular system updates and patching are critical in preventing vulnerabilities that can be exploited by malicious actors. By staying up to date with the latest software releases, IT departments can ensure that security patches are applied promptly, reducing the risk of data breaches.
Segmenting Networks To Limit Access
Segmenting networks is a proactive approach to limit access to sensitive data. By creating distinct zones within the network, organizations can control who has access to specific resources, reducing the likelihood of unauthorized access.
Implementing Firewalls And Intrusion Detection Systems
Firewalls and intrusion detection systems serve as the first line of defense against cyber threats. By actively monitoring network traffic and filtering out potentially harmful data packets, these tools help in safeguarding the organization’s data against unauthorized access and cyber attacks.
Backups And Disaster Recovery Strategies
Implementing robust backup and disaster recovery strategies is crucial to ensure data integrity and availability in the event of a cyber incident. Regularly backing up data and developing comprehensive recovery plans can minimize the impact of potential data loss or system failures.
Responding To Data Breaches
Data breaches can be a nightmare for organizations, causing significant damage to reputation, customer trust, and financial stability. Responding swiftly and effectively is crucial when it comes to mitigating the consequences of a data breach. In this article, we will explore the key steps involved in responding to data breaches, including creating an incident response plan, promptly investigating and containing breaches, notifying affected parties and authorities, and learning from breaches to strengthen security.
Creating An Incident Response Plan
An incident response plan serves as an organization’s blueprint for addressing data breaches. It outlines the roles, responsibilities, and procedures that need to be followed in the event of a breach. By developing a comprehensive incident response plan, you can ensure a coordinated and efficient response to any security incident. The plan should include:
- A clear chain of command and designated incident response team members
- Identification and classification of potential threats and vulnerabilities
- Predefined steps for isolating affected systems and networks
- Communications protocols for internal and external stakeholders
- A timeline for investigation, containment, and recovery efforts
Promptly Investigating And Containing Breaches
Once a breach has been detected, prompt investigation is crucial to identify the root cause, extent of the breach, and the affected systems or data. Immediate action should be taken to contain the breach and prevent further unauthorized access or data loss. This may involve:
- Isolating affected systems or networks
- Changing passwords and access credentials
- Applying patches and updates to close vulnerabilities
- Monitoring network traffic for ongoing suspicious activities
Notifying Affected Parties And Authorities
Notification is a critical step in responding to a data breach. Affected individuals must be promptly informed about the breach to take necessary actions to protect themselves. Additionally, certain jurisdictions may have legal requirements for notifying authorities about data breaches. When notifying affected parties and authorities:
- Clearly explain the nature of the breach, including what data has been compromised
- Provide guidance on potential risks and steps individuals can take to mitigate them
- Offer resources and support for affected individuals, such as credit monitoring services
- Comply with any legal obligations and industry standards in terms of timing and format of notifications
Learning From Breaches To Strengthen Security
Every data breach should be viewed as a learning opportunity to enhance security measures and prevent future incidents. After responding to a breach, it is important to conduct a thorough post-incident review, which involves:
- Identifying the vulnerabilities and weaknesses that allowed the breach to occur
- Implementing measures to address and mitigate the identified vulnerabilities
- Providing training and awareness programs for employees to prevent similar incidents
By continuously learning from breaches and actively enhancing security measures, organizations can proactively protect themselves against future threats.

Credit: www.electronicshub.org
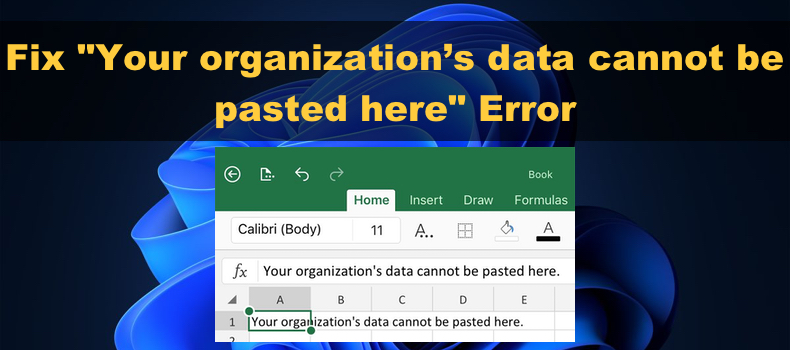
Credit: blog.pcrisk.com
Frequently Asked Questions For Your Organization’s Data Cannot Be Pasted Here.
Why Can’t I Paste My Organization’s Data Here?
Pasting your organization’s data here is not allowed for security reasons. We prioritize protecting your sensitive information and preventing unauthorized access. You can explore alternative methods, such as importing or exporting data securely, to share your organization’s information without compromising its security.
What Are The Risks Of Pasting Sensitive Data?
Pasting sensitive data can expose your organization to significant risks, including data breaches, unauthorized access, and potential legal repercussions. It is crucial to handle sensitive information with care and ensure proper security measures are in place to protect your organization’s data from falling into the wrong hands.
How Can I Securely Share My Organization’s Data?
To securely share your organization’s data, consider using encrypted file-sharing platforms, secure cloud storage solutions, or establishing password-protected access. By implementing these measures, you can ensure that only authorized individuals can access and interact with your organization’s sensitive information while maintaining necessary security protocols.
Conclusion
In light of the increasing importance of data security, it’s crucial to prioritize protecting your organization’s sensitive information. By enforcing strict data protection policies and investing in secure technologies, you can safeguard your data from potential threats. Take proactive measures to strengthen your organization’s data security and build trust with your stakeholders.




